Below are the steps to configure SIP integration between CUCM and Unity Connection. This is now the Cisco recommended best practice and replaces the legacy CTI Route Point configuration.
Create New SIP Trunk Security Profile
- In CUCM, navigate to System > Security > SIP Trunk Security Profile
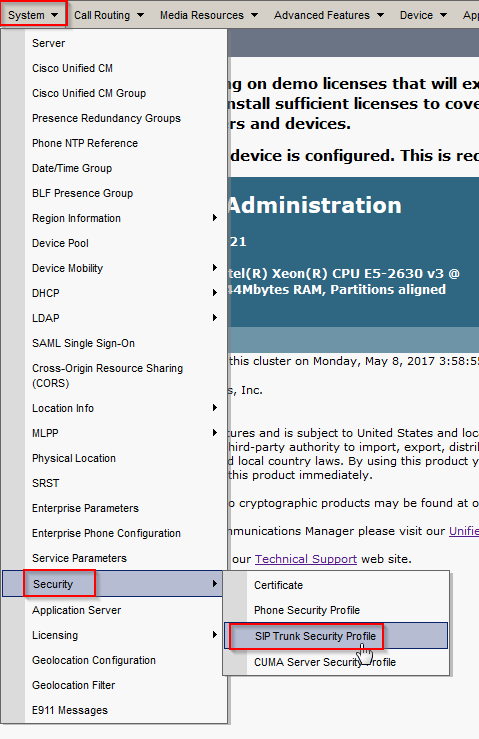
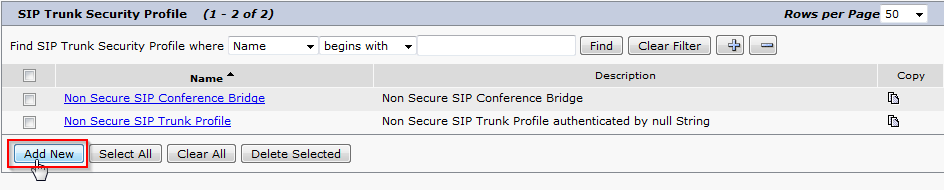
- Click Add New
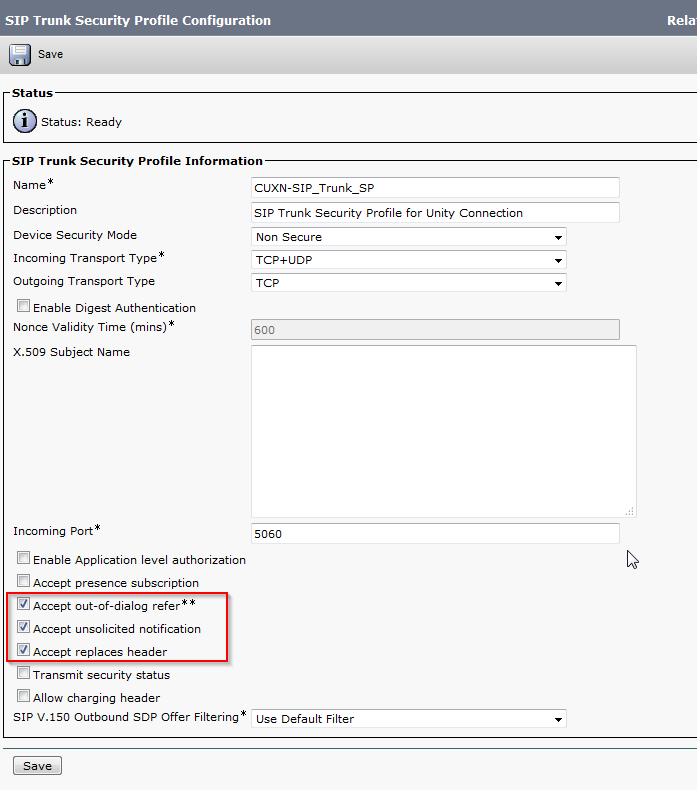
- Enter a Profile Name and Description, check Accept Out-of-Dialog REFER, Accept Unsolicited Notification, Accept Replaces Header. Click Save.
 Create a SIP Profile
Create a SIP Profile