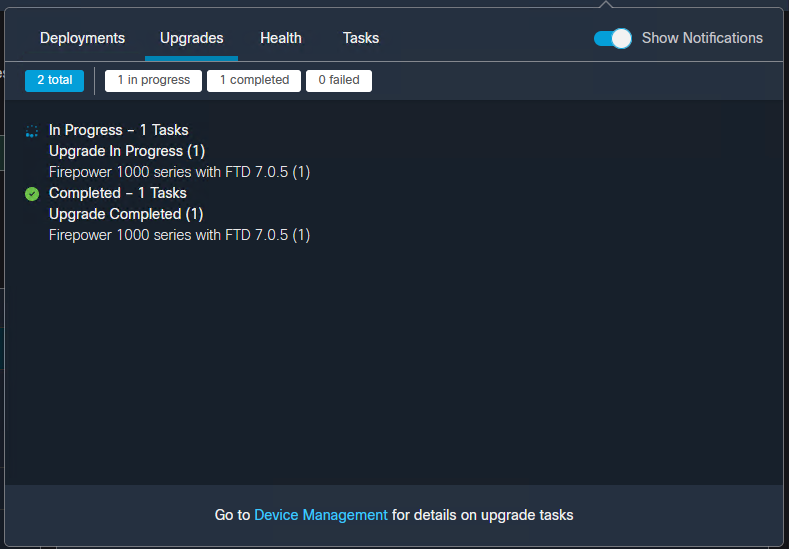
Often when deploying Firepower/Secure Firewall devices I get asked to show that everything is working as expected or to prove that things like the Snort IPS engine are working as advertised.
I can’t, in good conscience, attempt to download some malware or ransomware on their network but how about a simple ping?
Thankfully there’s a built in Snort rule (sid) that can be enabled to trigger a security alert on ICMP Echo Replies, so all we need to do to highlight Snort efficacy and alerting is to enable that particular sid and send some Echo Requests and wait for the Reply.